How Hackers Can Use BitTorrent to Control Your Computer

Torrents are used worldwide by a plethora of users, both for legal also as illegal activities. It is the about common peer-to-peer mode of file sharing, but that too means that there is no verification of information being transmitted. According to a contempo report, Manual, one of the best torrent clients out there, has been reported to be vulnerable to foreign hacks.
As reported by ArsTechnica, there happens to be a disquisitional weakness in the widely used Manual BitTorrent app that allows websites to execute malicious code on some users' computers. Tavis Ormandy, a researcher working with Google's Project Zero vulnerability reporting team, stated that at that place is a Transmission part that allows users to control the BitTorrent app with their Spider web browser.
According to Ormandy's proof-of-attack, using a hacking technique known as domain name arrangement rebinding, the Transmission interface tin be remotely controlled when a vulnerable user visits a malicious site. He states that his exploit works on popular web browsers such every bit Chrome and Firefox, and is applicable to both Windows and Linux.
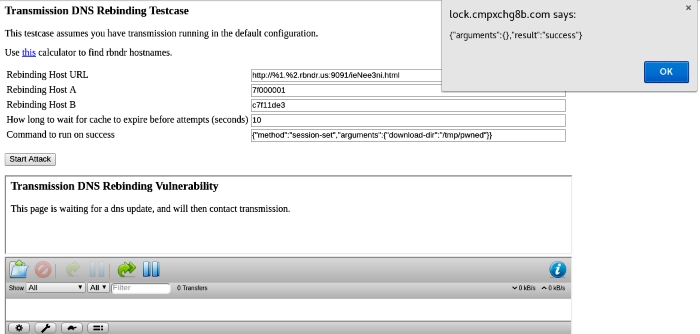
As per his exploit, attackers tin take control of users' systems by creating a DNS name they are authorized to communicate with so making information technology resolve to the localhost name of the vulnerable computer. In a split post while publishing the patch for the same, Ormandy stated the attack takes identify in the following manner:
- A user visits
http://assailant.com, which has an<iframe>to a subdomain the attacker controls. - The attacker configures their DNS server to respond alternately with
127.0.0.oneand123.123.123.123(an accost they command) with a very low TTL. - When the browser resolves to
123.123.123.123, they serve HTML that waits for the DNS entry to elapse (or forcefulness information technology to expire by flooding the enshroud with lookups), then they have permission to read and set headers.
Using the above exploit, the attacker can alter the Torrent download directory to the user'due south home directory and then make Manual download a Torrent chosen ".bashrc" which would automatically exist executed the next time the user opened a fustigate trounce. Attackers besides gain the ability to remotely configure Transmission to run any command of their choosing after a download has been completed.
Whatsoever vulnerability that is reported by Project Zero is unremarkably withheld for a flow of 90 days or until the programmer has released a set up before going public. That being said, the researcher has disclosed the vulnerability just xl days afterwards the initial written report, because the fact that "Transmission developers are not responding on their individual security listing." According to Ormandy, "I suggested moving this into the open so that distributions can utilize the patch independently."
While Ormandy understands that the threat is of "relatively low complication", he states that this is exactly the reason why he is eager to make certain everyone is patched.
In a response to ArsTechnica, a Manual development official stated that he expected an official fix to be released "ASAP" just was not specific. According to him, the vulnerability was nowadays only when users enabled remote access and disabled password protection.
As of at present, there is no official word on when will Transmission be releasing an update for the fix. That being said, we recommend the readers to enable password protection using the inbuilt the JSON RPC interface. Also, according to reports, other BitTorrent clients are also vulnerable to the same hack, so nosotros recommend users to use these torrent clients with caution, and non exit them running unattended.
Source: https://beebom.com/bittorrent-flaw-hackers-control-computer/
Posted by: armitageliciriand.blogspot.com


0 Response to "How Hackers Can Use BitTorrent to Control Your Computer"
Post a Comment